I really find it disturbing that even if you are completely fastidious about
purging temporary files, personal information can still be harvested from a
computer’s hard drive. What if you are on
vacation and happen to use an internet cafe’s computer? Or what if you are a
student using a PC in one of your school’s computer labs? If you go to a site that
requires a password or if you order something from the internet with a credit card,
that private information may or may not be obtainable by someone with harmful
intentions. The Stealth Surfer is a
product that completely does away with that worry, because it
basically hijacks the host computer and forces data that would ordinarily go
into a temporary file on the host’s hard drive, into a folder on the
StealthSurfer itself instead.
This year, the
StealthSurfer
I previously reviewed has undergone a major facelift, and the new
model is going by the name
StealthSurfer II. While the hardware remains (as best I can tell) exactly the
same, there have been so many improvements to the software portion of this
device that it is now world’s ahead of where it was. The StealthSurfer II is
available in 128MB, 256MB, 512MB and 1GB memory denominations. Once again, I was
sent the 128MB.

The new StealthSurfer II is on the top, the older model on the
bottom
In it’s plastic case, the StealthSurfer II (SSII) measures 2.52" long (including
the lid)
and 0.83" wide x 0.3" thick. If the reinforcing case is completely
removed, the SSII measures a secretive 1.7" long x 9.7" wide x 0.1" thick.

In this picture from last year’s review, you can see the dismantled
StealthSurfer
Specifications:
Interface: USB 2.0, data transfer rate up to 480Mb/sec
Capacity: 128MB ~ 1 GB
Sustained Data Transfer Rate: Up to 8MB/sec
OS Supported: Win 2000/XP
Power Supply: DC 5V/3.3v +/-5%, through USB port
Power Consumption: <140 mA
LED Indicator for file access
One of the many great features of the StealthSurfer is that it can also be
used as secure flash memory for moving the owner’s files from one computer to
the next. The only limits are the size of the installed memory, in this case
approximately 128 MB.
Since there is not much that wasn’t already covered in the previous review
concerning hardware, let’s jump right into the software.
What sets the SSII apart from the first generation model is that it now
includes everything anyone might need for complete privacy and
convenience while surfing. Self-contained inside the SSII are licensed versions
of the following:
Firefox – a popular high-speed browser with enhanced security
Anonymizer – offers anonymous surfing, complete network security and IP
masking
RoboForm – a "one-click" form-fill with secure user ID/password
management application
Thunderbird – for portable POP3/SMPT email, news groups,
RSS feeds, and blog
access
Hushmail – a high security web based e-mail solution
Setting up the SSII is done by plugging the device into an available USB port
on a computer running Windows 2000 or XP. The StealthSurfer is not compatible
with earlier versions of Windows or Windows NT, and it does not work with the
Mac OS. Yes, I can hear the boos and hisses now, but every now and then it is
nice for us Windows users to get the cool stuff! ;0)
When the SSII is installed, the following screen will appear showing the
gateway to the contents of the disk.
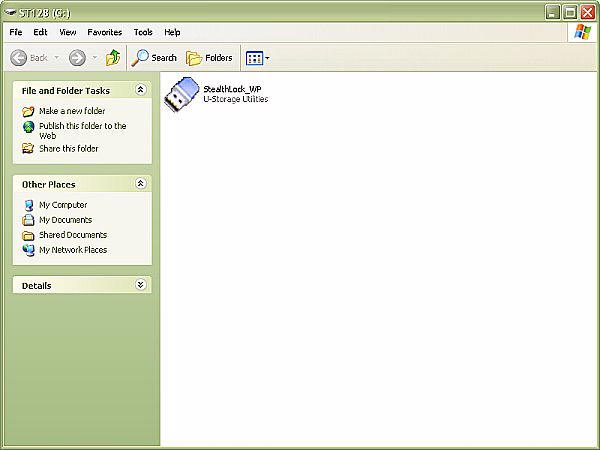
Clicking the StealthLock icon prompts the user to enter their password, which
is set with a default of "1111". Obviously this default password should be
changed immediately to something specified by the user. A hint can also be
entered if you are the the forgetful type.
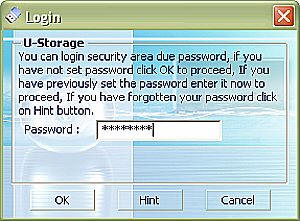
When an incorrect password is entered, the screen will mention it. Up to
three tries may be made before the StealthSurfer must be removed and reinserted,
essentially causing it to reset in order to allow the user to try again. The
data stored inside is completely protected by 3DES encryption, and there is no
way to access it without destroying the device.
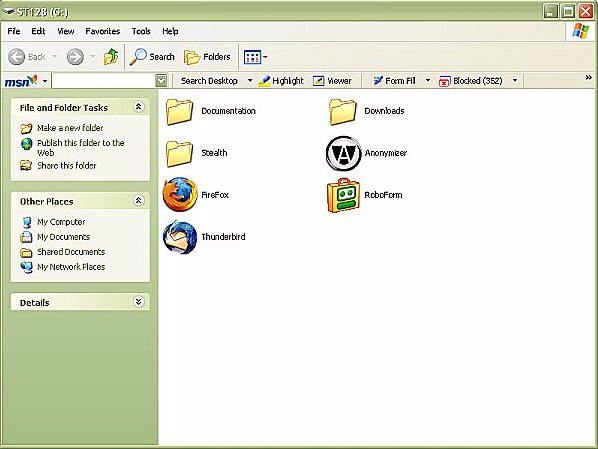
Once the password is entered, the following screen is revealed, which
includes icons for the various included programs. The only one not showing is
Hushmail, which is a web-based email accessed through the Firefox browser from
the StealthSurfer front page.
As each program is run, a corresponding icon will be displayed in the host
computer’s system tray. From left to right (after the WeatherBug temperature
readout) are: Anonymizer, RoboForm and the icon showing that the StealthSurfer
is installed and running.

Firefox Browser:
Recently I decided to stop being the last Internet Explorer holdout, and I began
using Mozilla’s Firefox browser. One of
the things that I appreciate about Firefox is its clean design, speed and lack
of tolerance for spyware and popups. It was a nice surprise to find that the
SSII included integrated Firefox, allowing me to use my now favorite browser –
including all of my bookmarks – from any computer anywhere in the
world…without leaving a trace.
When the user is browsing the internet with the SSII drive installed
"all
cookies, cached files and other downloaded images are stored privately" on
the SSII. All of the unavoidable downloaded images and data are trapped by
the SSII. You can view them in the Stealth/cache/Cache folder.
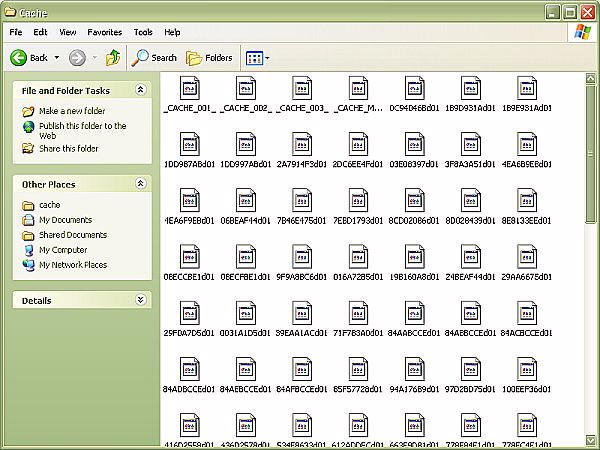
The results of less than five minutes of surfing!
Even though there a start-up sequence as the Firefox browser is activated, I do
miss seeing something on the actual browser screen that indicates my
stealthy surfing. The previous model SS had a stealth fighter icon in the upper
right hand corner, which while primitive was reassuring.
Be sure to clean out your cache folder occasionally, especially if you only have
the 128MB model! This can easily be done through the Firefox browser, by going
Tools/Options/Privacy/Cache/Clear.
Anonymizer:
According to the StealthSurfer site, "Anonymous Surfing safeguards a
user’s identity and Internet activities by shielding their IP, or Internet
address, from hackers and online snoops. An encrypted path is created between a
user’s computer and the Internet using 128-bit SSL technology, the most secure
form of SSL available, to ensure the highest level of protection and anonymity.
Anonymous Surfing defends users from the most prevalent Internet privacy and
security threats, including online identity theft, phishing attacks, and online
tracking. When used from a wireless-enabled laptop, Anonymous Surfing secures
all data sent over a wireless connection while surfing at home, at work or at
the local coffee shop.
The program is activated with
the click of a single button and works silently in the background without
slowing the Internet connection."
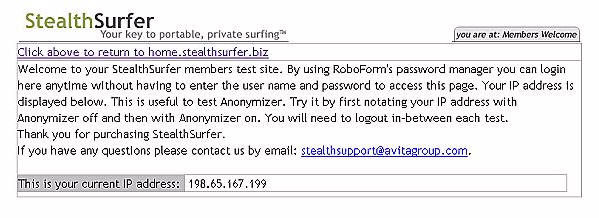
Putting it in layman’s terms, when I activate Anonymizer,
my IP number is no longer recognizable as belonging to Cox.net in San Angelo,
Texas. You can test and see what IP is being displayed by going to
a members only location on the StealthSurfer site.
According to Melissa Data, that IP address equals this information:
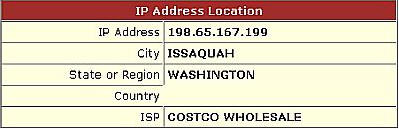
I checked my IP from two internet forums where I have administrative powers, and
sure enough – I am now located in Washington! This means that I can post in
forums without logging my correct IP, as well as surf the internet without
leaving data tied directly to my true IP. I think this is simply amazing!
RoboForm:
According to the StealthSurfer site, "This
integrated tool simplifies the process of filling out online forms by storing
multiple user identities, including name, address, phone number, and other
important information required by the user; it also securely stores confidential
data such as passwords, bank accounts, and credit card numbers."
Located at the top of the SteathSurfer’s browser window is a toolbar with all of
the RoboForm options. If you are already using Firefox and you ever accidentally
don’t close out all of your browser windows before plugging the SSII in, then
you will know things aren’t secure because this toolbar will not be showing.

The beauty of the RoboForm utility is that it will save your passwords as you
enter them into various site forms, and it will remember them later allowing for
speedy access. This program can also generate strong passwords, if you are not
feeling particularly inspired.
When a site is accessed that requires a password, a form will pop up asking if
the user would like to save the login and password information…
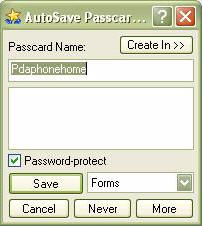
The Passcard name is editable, so if you have several passwords for different
zones on the same site, they can be kept separate without overwriting each
other.
Once the password is saved, the website will be immediately accessible when
the RoboForm feature is being used, either by selecting Logins and clicking on
the wanted site or by simply clicking on the login page. The password will also
be recalled the next time the login page is accessed from within the
StealthSurfer browser.
Thunderbird:
According to the StealthSurfer site, with Thunderbird you can, "Access an email account
anywhere at anytime. Thunderbird gives users a faster, safer and more productive
email experience. Designed to prevent viruses and to stop junk mail, this tool
is portable and can secure both POP mail (such as through Outlook or Outlook
Express) and Web-based email. POP3/SMPT email, news groups,
RSS feeds, and blogs are all easy to set up and use with Thunderbird."
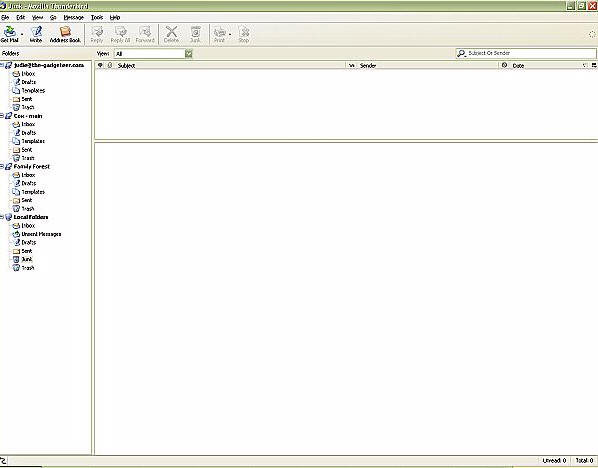
Now here is something that I have truly been needing. Every time I go
out of town, it is an absolute chore to check my Gadgeteer email account
because without my Outlook spam-filter, I easily get four or five hundred pieces
of junk mail a day which I then have to wade through. Using the Mozilla
Thunderbird email client, I was able to easily import my Outlook email settings,
and Thunderbird’s intuitive built-in spam filter has been doing a very
good job of keeping things manageable. Importing my contacts was a bit trickier,
even using the Outlook and Thunderbird wizards, but I eventually got things
sorted through.
More than any other feature – Thunderbird is the one that makes the
StealthSurfer II a "must have", in my opinion. Being able to leave home
and travel with all of my email accounts and contacts stored on an encrypted
device, allowing me to retrieve my email from almost any computer in the world
securely…I am
verklempt!
The Mozilla Thunderbird GUI is very nicely laid out, easy to manage, and
aesthetically pleasing. I wish I had a larger capacity StealthSurfer II, as I
would seriously love to import all of my email storage folders over to
the StealthSurfer and use it as my default method. Ah well, I am sure there are
downsides to doing that…
Anyway! I should mention that Thunderbird and the StealthSurfer II are not
trying to help spammers in any way, therefore your IP address is not masked when
you send email from the Thunderbird email client.
Hushmail:
At the bottom of the StealthSurfer welcome page, inside the Firefox browser, is
a login area for Hushmail, a private internet based email included with the
StealthSurfer II.
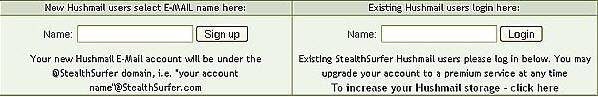
Since there aren’t all that many users yet, I was actually able to get the
email I wanted – my name @stealthsurfer.com. Coolness! 2MB of storage are
included for free, but larger storage options are also available for a fee.
After signing in for the first time, you are prompted to enter a password so
that Hushmail can start working it’s encryption magic on your account.

Next, this cryptic (no pun intended) java application starts…
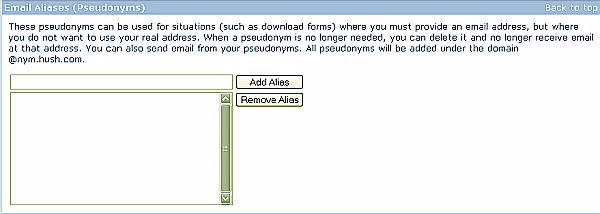
…and finally you are allowed to enter the email twilight zone. A place from
which you can even generate pseudo-alias email accounts which receive mail…
According to the SS site, "Sending an
unencrypted E-Mail is like posting a letter without an envelope. The information
you receive and transmit can be routinely monitored, logged, analyzed and stored
by third parties. In addition to the basic human right to privacy, E-mail users
must consider the importance of keeping business communications secure from
rival organizations and should only send data in an encrypted format. The same
concerns apply to the transmission of medical records, sensitive legal, military
or personal information. Every time you send E-mail, you trust your messages and
privacy to nameless and faceless individuals or organizations that frequently
have no guidelines and no concerns for your privacy or security.
By contrast,
StealthSurfer integrated Hushmail keeps your online communications private and
secure. Not even a StealthSurfer or Hushmail employee with access to our servers
can read your encrypted E-Mail, since each message is uniquely encoded before it
leaves your computer. A StealthSurfer Hushmail account lets you communicate in
total security with any other Hush member anywhere in the world.
Hush E-Mail uses industry standard algorithms as specified by the Open PGP
standard (RFC 2240) to ensure the security, privacy and authenticity of your
E-Mail. With Hushmail, users need only create and remember their own
passphrases, and the secure Hushmail server does the rest. Encryption and
decryption are transparent to the user, making Hushmail the most user-friendly
secure mail solution available. Through the Hush Encryption Engine™, the Hush
key servers take care of Public/Private key exchange in a completely seamless
fashion. When a user wishes to encrypt/decrypt data or verify/sign a
signature, a connection is automatically made to a Hush Key Server to retrieve
the necessary Public/Private Key."
Obviously, this is some super encryption that the average email user doesn’t
need. For my use, 2MB is more than generous – it’s not like James Bond is
sending me email every day or anything. However, if you happen to belong to an
organization that uses acronyms for its name, then you might enjoy having a
larger account. For the rest of us, 2MB of super encrypted security in
addition to the non-encrypted (but still totally self-contained) Thunderbird
email client should be sufficient.
If you are unsure about whether or not the StealthSurfer is something you
would use, then you can actually
try one for
free. I noticed this blurb on the bottom of their ordering page, "As a
limited time special offer try your StealthSurfer FREE! With this
special offer we will ship you a 128MB StealthSurfer for a small processing
fee plus shipping and handling. For any reason if you are not completely
satisfied just return your StealthSurfer within 30 days and you will not be
charged." Through the member’s site, people that bought the original
version StealthSurfer can upgrade to the StealthSurfer II (in the same memory
denomination) for $25 by sending in theirs and a copy of their original order.
If you use a Windows 2000 or XP computer either at home, at a friend’s house,
at the library, in a computer lab at school or in internet cafes, then you
have got to give this gadget a try. It has earned a permanent home in
my gear bag, and you had better believe that I will never travel
without it again.
You can read more about how the StealthSurfer II works
here.
The StealthSurfer FAQ may be viewed
here.
The online manual and other support information may be viewed
here.
Price: $99.29 (for 128MB), up to $299.29 for 1GB
Includes a 30 day money back guarantee and a one year limited warranty against
physical defects in material and workmanship
Pros:
Password protected memory card storage in varying denominations
Built-in browser and cache files to trap all surfing activity
Improved software that makes all internet and email activity invisible to the
host computer
Ability to carry favorites from computer to computer
Cons:
Does not work on Mac computers
Does not work on PCs running Windows 95, 98, Me or NT
Product Requirements:
A 1.1 or 2.0 USB port, IBM or compatible PC
running Windows 1000/XP
Product Information
| Price: | 99.29 |
| Manufacturer: | StealthSurfer |
| Pros: |
|
| Cons: |
|

Gadgeteer Comment Policy - Please read before commenting
significant improvement to other vm drives.
portable, fast transfer rate and 3des protection.
After an analysis and test, we found the results to meet and exceed mfgs stated numbers.
We would like to see the device encased in an ironkey housing and have its added encry alig’s added to it to make it the rolls royce of portable hdee drives.
perfecto!