Product Requirements:
Windows XP, 25MB free disk space, One
free USB port
Back in the late 70’s and early 80s, my parents trusted me to stay in the
house by myself and not invite friends over when I was left at home alone. There
really wasn’t that much I could do that would put me (or my parents) in
danger – as long as I kept the front door locked. Computer usage was restricted
to programming my TRaSh-80 with inane BASIC commands and to playing Space
Invaders or Asteroids on my Atari VCS. There wasn’t much I could do from home
that would get me into trouble – unless you count prank calls, but that’s
neither here nor there. In a time before caller ID, I could still get away with
things like that. ☺
In 2004, the internet is such a part of our daily lives that it is not
uncommon for children to have their own email accounts and web sites that they
enjoy visiting. Many kids even have their own computers, just so that mom or dad
don’t have to share theirs. Just as the television was accused of being my
generation’s electronic babysitter, the same might be said about the internet
and this generation.
The very idea of today’s internet would have boggled my brain at 14 (1981,
for those that were wondering). Being able to chat with complete strangers from
across the world, getting instant messages and email from people I knew (and those I didn’t), as well as being able to look up information on any
subject that my teen-aged mind found interesting…well – it would have been
almost as fun as sneaking out of the house, or sneaking someone else in.
Now that I am the parent of a 14 year old daughter, I am in a situation my
parents could have never imagined – and it puts me in a quandary. On the one
hand, I am positively thrilled that Sarah loves computing and
spending time on the internet. As a Gadgeteer, it warms my heart to see her taking an
interest in something I enjoy so much myself. I want her to be excited about
everything having to do with consumer electronics. I am proud of
the fact that she knows more about the inner workings of a computer than I do,
and I am slightly jealous that unlike me, she is a touch typist – or keyboardist
– or whatever it is called these days.
On the other hand, I can’t help but worry about the amount of time she would
spend on the web if I allowed her to enjoy it to her heart’s content. We have
actually had to limit her to an hour a day, with extra time earned for good
grades or time taken away for the rare poor grade. Otherwise, I think she would
be on it every waking hour that she wasn’t in school or with friends. She is
fearful of being grounded from the internet in the same way I was fearful of
being grounded from the TV, back in the day.
I would like to state right now that I trust Sarah. I don’t think it has even
occurred to her to Google some of the subjects I might have been tempted to
"research" when I was her age. Her idea of a chat room is the discussion board
at NeoPets. But even so – when I can hear
her from across the room clacking on her keyboard, and I know that she is IM’ing
a "friend", I still feel the need to tell her not to give out any personal
information – that the 14 year old girl she thinks she is talking to might
actually be a 41 year old man. Eck.
With the stories we have all heard over the last few years of tragedies
occurring because kids were allowed unsupervised and unlimited access to the
internet, it is not unreasonable for a parent to want to at least be home
or in the same room when their child is online. It is important that parents set
guidelines for when their child can be online, and it is crucial that there be a
real way of enforcement. I am not talking about spying on your teenager or
installing some Orwellian software that allows you to see what they are saying
when they are IM’ing their friends. I would never suggest that. What I am
talking about is an item that can give you peace of mind – knowledge that your
child can only access the internet with your knowledge and permission.
How? With the Griffin Technologies Parental Internet Control
Key.
The Control Key is a small USB plug capped with a blue plastic handle.
Measuring only 2" x 0.7", it can easily be attached to your key ring with the
split metal ring on its end.

The Control Key comes with an installation CD that walks you through setup,
which we will recreate here…
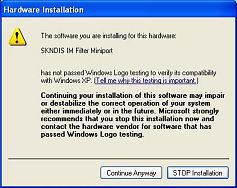
When I first ran the CD, I got one of those pesky XP compatibility issue
windows. Unperturbed, I clicked "Continue Anyway."
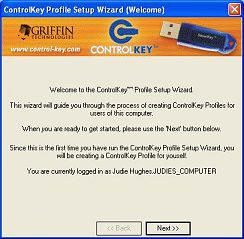
The next window shows how you are currently logged in, and informs you that
you are about to create a new profile for this user…
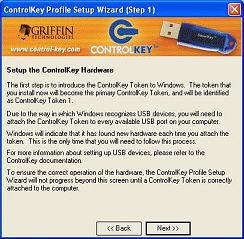
This screen explains how you will have to introduce the Control Key "token"
to Windows. You will attach this "token" to every USB port on the computer in order to complete the lock-down. This is
the only time you will ever have to do it, but in order for the key to work from
any port, you must set it up on each one.
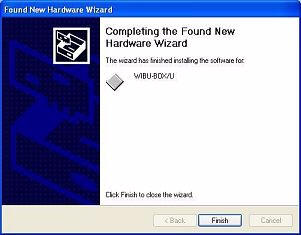
So here, you can see that I have inserted the Key in my first USB port…

Each time the Key is inserted in a USB port and the "token" is installed, the computer detects it as new
hardware and runs the Found New Hardware Wizard. Drivers will install from the
CD, and then you will advance to the next port following the same steps.
Once you have inserted the Key into every USB port, run the hardware wizard and are ready to
continue, this window will pop up. It asks if you are sure that you
installed a Control Key token on ever USB port on your computer.
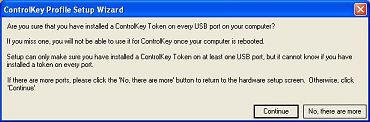
By now, you might be wondering why it is so important to run the key in every
port; I admit that I was. I thought that maybe it was because the key could
be defeated somehow if each port wasn’t configured, but that is not the case. It
simply means that you won’t be able to insert the Key in an unconfigured port
and expect it to unlock. If your computer is like mine, with ports on the front
and back of the CPU case, you might decide to be lazy (as I was) and just
configure the Key to work in the front ports.
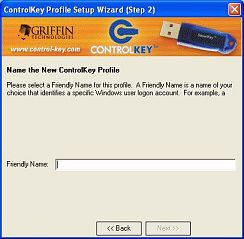
Next, you will assign a "friendly name" to the profile you are creating. I chose
"Mom." I suppose I could have been more imaginative and done "Big
Brother" or the like…
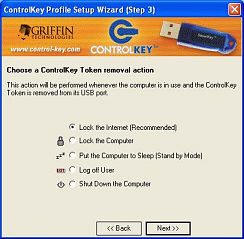
Now is the point where you chose what will happen when you remove the Key.
You can set it so that the following occur:
1. Lock the Internet – immediately. This is great if you want your child to still be able to
use their computer, just without any online access (no IM, email or web
pages). It is important to note that
if the computer is shut down and restarted without the key, then computer
access has effectively been lost. More on this later…
2. Lock the Computer – immediately
3. Put the Computer to sleep (standby mode) – immediately
4. Log off user – immediately
5. Shut down the computer – also immediately
I selected Lock the Internet…
At this point I should say that whatever selection you make, the minute you
pull that key out it will take effect. Talk about instant gratification!
This screen verifies your choice and reminds you that the Key is required to
access your chosen action.
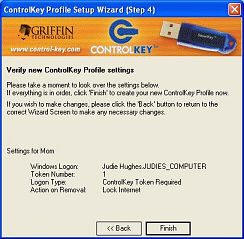
Clicking Finish, you get this message: The next time you start your computer,
you will have to use your Control Key to log in.
![]()
![]()
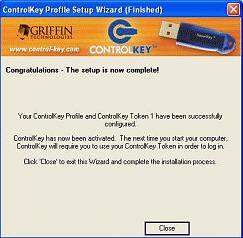
This part is extremely important…let’s say you have set your Key to shut
the computer down when it is absent, and then one day while you are out and
about…you lose your Key! You
are looking at some serious downtime, because your key has it’s own unique
serial number. So for goodness sakes, do the 30 second internet registration
option. This way Griffin Technologies has your number and they can straighten
out the mess if you lose that Key.
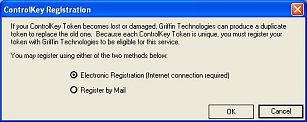
After registering, it is time to restart.
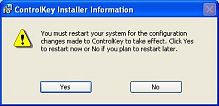
When your computer comes back up, you will see this screen first…
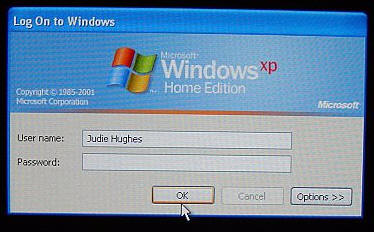
I don’t have a password assigned, so
I just hit "OK"
Without the Key inserted, this is the next screen you’ll see…
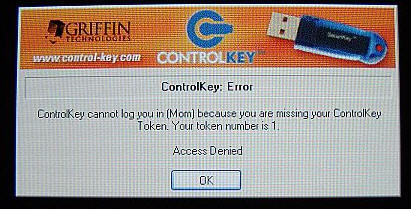
This is what I meant when I said earlier that restarting the computer without
the Key – even if you only have it on Lock the Internet" – will effectively deny
access to the computer. Since I have the key, it’s no big deal to slide that
sucker in and gain immediate access. If your child was home alone working on a
report and the computer froze, necessitating a restart, then you could probably
expect a rant waiting for you when you returned. Small price to pay, if
you wanted to make sure your child wasn’t chatting with strangers the whole time
you were gone, though – wouldn’t you say?
The first time you restart after installation and registration, when you
check your email there should be a letter confirming that Griffin Technologies
has received your registration. At least now you know that if you lose your key,
they will be able to help you unlock your computer…
So what about ways to defeat the Control Key? Let’s say your child is gifted
with computer skills, will he or she be able to get past the Key?
The first thing I checked was to see if there was an installed program now
located on my computer that could be removed from the Add or Remove Programs
control panel…and there was. Clicking "Change" (with the Key removed from the
USB port) brought up a window asking if I would like to Modify, Repair or Remove
the program. Remove…then nothing. The Add or Remove Programs window froze and
started beeping every time I clicked on it. Nothing else on the computer was
frozen – just the Add/Remove window. It would have been more fun if there had
been the image of an old lady going, "tsk-tsk" while shaking her finger,
but it was just as effective. After a minute or so, the following window popped
up…
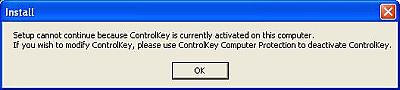
Not too shabby.
There are a couple of changes to the way I sign in and out that have been
made since installing the Control Key. For instance, when I go to Start/Shut
Down, I no longer get the three choice graphic of "Stand By" "Turn Off" or
"Restart." Instead, I see this…
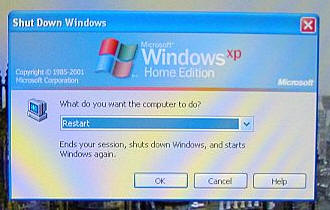
From which I can choose: "Log Off Judie Hughes", "Shut Down", "Restart",
"Stand By" and "Hibernate."
If I choose to Restart, I get the following pop-ups windows…
and…
Here’s where the Parental Internet Control Key gets really interesting –
check out these screen shots and their options…
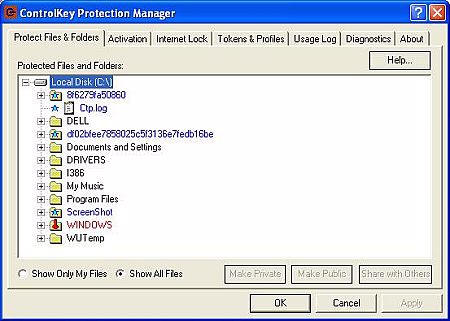
You can actually specify certain files and folders that you don’t want
anyone to have access to without the key…
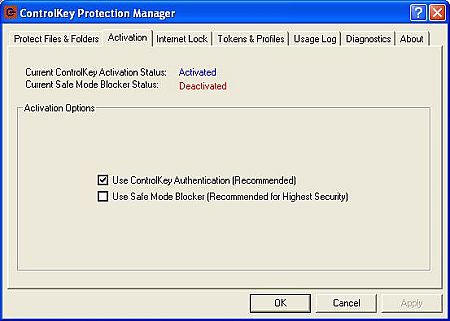
You can chose different levels of protection…
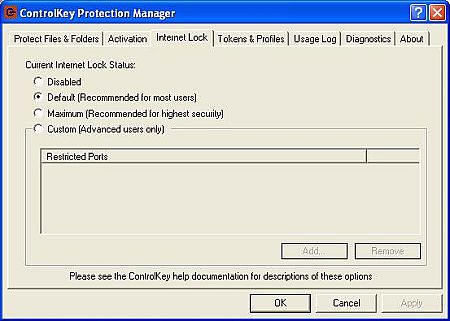
You can turn the Internet lock on or off, or restrict ports to your
specifications…
You can also manage "tokens" on the computer, to work with various
profiles…
![]()
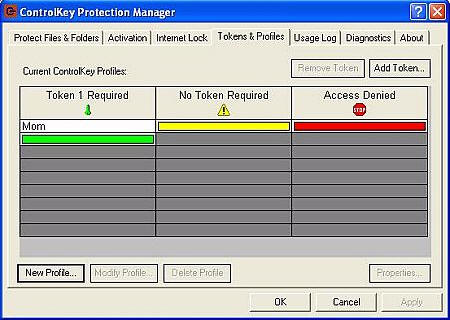
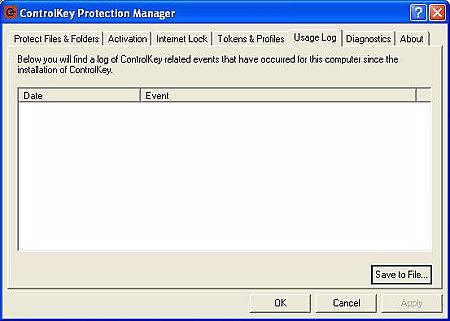
There is also a log for Control Key related incidents – not that I have
amassed any yet…
The Parental Internet Control Key is genius! I can think of so many scenarios
where it could come in handy. Here are just a few:
1. It is small enough that you could install it in a rear USB port with no
one the wiser, leaving it dangling for as long as your child follows your rules
regarding internet usage. Should you find that your rules weren’t being
followed, then the net could mysteriously go down indefinitely – simply
by your removal of the Key.
2. If like me, you have found that the most effective punishment for your
teen is grounding them from the computer, you could simply remove the key
– replacing it when the grounding ends.
3. If you want to closely monitor when your kid gets on or off the computer,
then you can insert or remove the Key as you see fit.
Heck, I can see uses for the Control Key even if you aren’t a parent. What a
cool way to safely walk away from your desktop, knowing that no one is going to
be able to snoop into your files!
While there may be those that will argue that the price seems steep for such
a tiny product, I would have to argue that as a parent, it is very inexpensive
peace of mind.
Price: $59.99
Pros:
Non invasive way to supervise your child’s online time – without "spying"
Configurable access can be set to various options, including locking the
internet or keeping the computer shut down
Cons:
Does not work on Apple computers
If computer is restarted without the key, the key is needed to log back in under
your profile
Potential for computer downtime if the key is lost
HP 14 Laptop, Intel Celeron N4020, 4 GB RAM, 64 GB Storage, 14-inch Micro-edge HD Display, Windows 11 Home, Thin & Portable, 4K Graphics, One Year of Microsoft 365 (14-dq0040nr, Snowflake White)
(as of February 18, 2026 23:30 GMT -06:00 - More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)Dell 15 Laptop DC15250-15.6-inch FHD (1920x1080) 120Hz Display, Intel Core i5-1334U Processor, 16GB DDR4 RAM, 512GB SSD, Intel UHD Graphics, Windows 11 Home, Onsite Service - Platinum Silver
(as of February 18, 2026 23:39 GMT -06:00 - More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)Product Information
| Price: | 59.99 |
| Manufacturer: | Control Key |
| Pros: |
|
| Cons: |
|


